

Key security measures for back office operations include implementing strong access controls, regularly updating and patching software, conducting regular security audits, and implementing robust network security measures. Access controls should include strong passwords, multi-factor authentication, and role-based access control to ensure that only authorized individuals have access to sensitive data and systems. Regular software updates and patches are essential to address any vulnerabilities that may be exploited by attackers. Security audits should be conducted regularly to identify any weaknesses or gaps in the security measures. Network security measures such as firewalls, intrusion detection systems, and encryption should be implemented to protect data in transit and prevent unauthorized access.
CCTV Security Camera Placement Strategies for Commercial Properties
Back office data can be protected from unauthorized access through various measures. Firstly, access controls should be implemented to ensure that only authorized individuals have access to the data. This can include strong passwords, multi-factor authentication, and role-based access control. Secondly, data encryption should be used to protect the data from being intercepted or accessed by unauthorized individuals. Encryption ensures that even if the data is intercepted, it cannot be read without the encryption key. Additionally, regular backups should be performed to ensure that data can be restored in case of any unauthorized access or data loss. Network security measures such as firewalls and intrusion detection systems should also be implemented to prevent unauthorized access to the network.
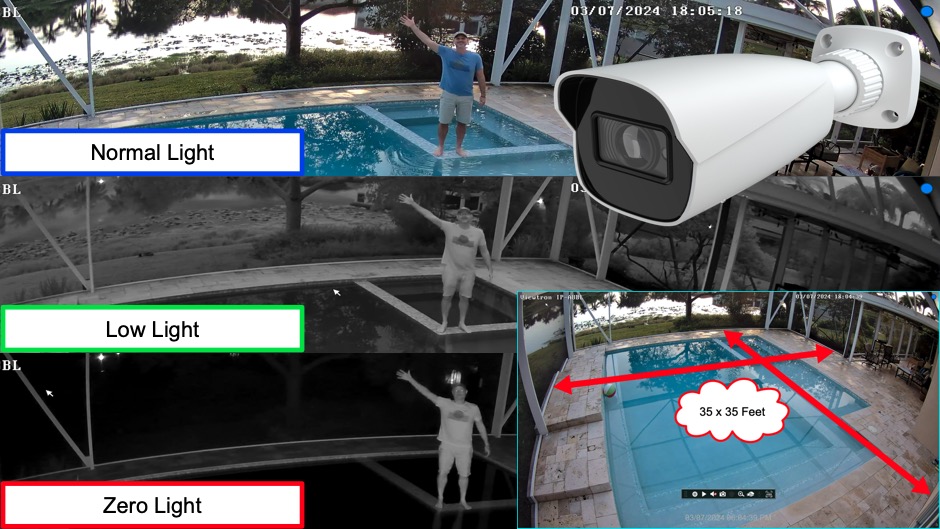
4K IP Camera: 2.8mm Lens Angle of View & IR Night Vision Testing The post 4K IP Camera: 2.8mm Lens Angle of View and IR Night Vision Testing first appeared on Security Camera & Video Surveillance Blog.
Posted by on 2024-03-12
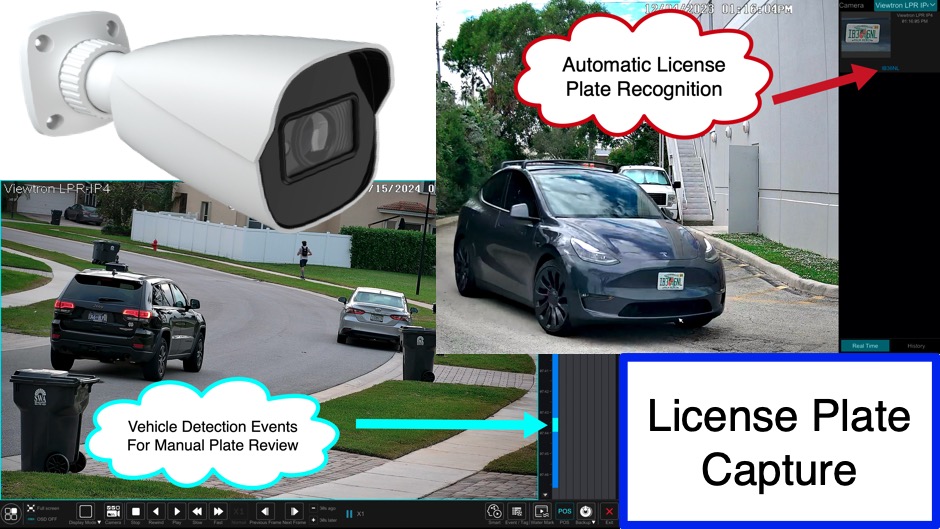
Night Time License Plate Capture w/ Viewtron LPR Camera The post Night Time License Plate Capture w/ Viewtron LPR Camera first appeared on Security Camera & Video Surveillance Blog.

Posted by on 2024-01-23
License plate capture camera and AI security camera vehicle object detection work great together. The post License Plate Capture Works Great with AI Security Camera first appeared on Security Camera & Video Surveillance Blog.
Posted by on 2024-01-17
This Viewtron LPR camera works on home installation at extreme angle and distance. The post LPR Camera Home Install License Plate Reader Software Test first appeared on Security Camera & Video Surveillance Blog.

Posted by on 2024-01-12
Encryption plays a crucial role in back office security by ensuring the confidentiality and integrity of data. Encryption transforms data into an unreadable format using an encryption algorithm and a unique encryption key. This ensures that even if the data is intercepted or accessed by unauthorized individuals, it cannot be read without the encryption key. Encryption also helps to protect the integrity of the data by detecting any unauthorized modifications or tampering. By encrypting back office data, organizations can ensure that sensitive information remains secure and protected from unauthorized access.

Common security threats faced by back office systems include malware attacks, phishing attacks, insider threats, and data breaches. Malware attacks can include viruses, ransomware, and spyware, which can compromise the security of back office systems and steal sensitive data. Phishing attacks involve tricking individuals into revealing their login credentials or other sensitive information through fraudulent emails or websites. Insider threats refer to the risk of employees or contractors intentionally or unintentionally compromising the security of back office systems. Data breaches can occur due to vulnerabilities in the system, weak access controls, or human error, resulting in unauthorized access to sensitive data.
Back office security can be integrated with overall organizational security measures by aligning policies, procedures, and technologies. This can include implementing a comprehensive security framework that covers all aspects of the organization's operations, including the back office. Security policies and procedures should be developed and communicated to all employees to ensure consistent adherence to security measures. Technologies such as network security tools, encryption, and access controls should be implemented across the organization to protect back office systems and data. Regular security audits and assessments should be conducted to identify any gaps or weaknesses in the overall security measures and address them promptly.

Best practices for securing back office networks and systems include regularly updating and patching software, implementing strong access controls, conducting regular security audits, and training employees on security awareness. Regular software updates and patches are essential to address any vulnerabilities that may be exploited by attackers. Strong access controls should include strong passwords, multi-factor authentication, and role-based access control to ensure that only authorized individuals have access to sensitive data and systems. Regular security audits should be conducted to identify any weaknesses or gaps in the security measures. Employee training on security awareness should cover topics such as recognizing phishing attacks, using secure passwords, and reporting any suspicious activities.
Employee training and awareness play a crucial role in back office security. Employees should be trained on security best practices, such as recognizing phishing attacks, using secure passwords, and following proper data handling procedures. By educating employees about the importance of security and the potential risks they may face, organizations can empower them to be proactive in protecting back office systems and data. Regular security awareness training sessions should be conducted to keep employees updated on the latest security threats and preventive measures. Additionally, employees should be encouraged to report any suspicious activities or potential security incidents to the appropriate authorities. By fostering a culture of security awareness, organizations can significantly enhance the overall security of their back office operations.

Yes, there are specialized cameras designed specifically for exterior perimeter surveillance. These cameras are equipped with advanced features and technologies to ensure effective monitoring and security of outdoor areas. They are built to withstand harsh weather conditions and have robust housing to protect them from vandalism and tampering. Some of the key features of these cameras include high-resolution imaging, wide dynamic range, infrared night vision, and long-range zoom capabilities. They also often have intelligent video analytics, such as motion detection and object tracking, to enhance their surveillance capabilities. Additionally, these cameras can be integrated with other security systems, such as alarms and access control systems, to provide a comprehensive perimeter security solution.
Ensuring security for museum exhibits through CCTV can be achieved by implementing a comprehensive surveillance system that incorporates advanced features and technologies. Firstly, it is crucial to install high-resolution cameras strategically positioned to cover all areas of the museum, including entrances, galleries, and storage rooms. These cameras should be equipped with motion detection capabilities, enabling them to detect any suspicious activity and trigger real-time alerts. Additionally, the use of infrared cameras can provide enhanced visibility in low-light conditions. To further enhance security, the CCTV system should be integrated with access control systems, allowing only authorized personnel to access restricted areas. Regular maintenance and monitoring of the CCTV system are also essential to ensure its optimal performance and to promptly address any technical issues. By implementing these measures, museums can effectively safeguard their exhibits and deter potential theft or vandalism.
Ensuring security at pharmacy counters through CCTV can be achieved by implementing a comprehensive surveillance system that incorporates various advanced features. Firstly, it is crucial to install high-resolution cameras strategically positioned to cover all areas of the pharmacy counter, including the cash register, medication storage, and customer interaction zones. These cameras should have night vision capabilities to ensure visibility in low-light conditions. Additionally, the surveillance system should include motion detection technology, which can trigger alerts and recordings when any suspicious activity occurs. Integrating facial recognition software can further enhance security by identifying potential threats or unauthorized individuals. Furthermore, the CCTV system should be connected to a secure network and have encrypted data transmission to prevent unauthorized access. Regular maintenance and monitoring of the system are essential to ensure its effectiveness and address any technical issues promptly. By implementing these measures, pharmacies can significantly enhance security at their counters and deter potential criminal activities.
To ensure security in food preparation areas, it is essential to implement strict hygiene protocols, such as regular handwashing, wearing protective clothing, and using disinfectants to clean surfaces. Additionally, it is important to properly store and handle food to prevent contamination and spoilage. Employing proper food handling techniques, such as separating raw and cooked foods, using separate cutting boards for different food types, and maintaining proper cooking temperatures, can also help ensure food safety. Regular maintenance and cleaning of kitchen equipment, as well as proper waste disposal, are also crucial in preventing the spread of bacteria and other contaminants. Training staff on food safety practices and conducting regular inspections can further enhance security in food preparation areas.
To ensure comprehensive surveillance on gaming floors, a casino can implement a robust security system that incorporates advanced video surveillance technology. This system should include a network of high-resolution cameras strategically placed throughout the gaming area, covering every angle and ensuring maximum visibility. Additionally, the system should be equipped with facial recognition software, motion sensors, and advanced analytics capabilities to detect any suspicious activities or behaviors. The security personnel should be trained in monitoring the surveillance feeds and identifying potential threats or fraudulent activities. Regular audits and inspections should be conducted to ensure the system's effectiveness and to identify any areas that may require additional surveillance coverage. By implementing such a comprehensive surveillance system, a casino can enhance the safety and security of its gaming floors, protecting both the players and the establishment itself.
When it comes to camera placements for garden centers, there are several key areas that should be considered. One important location is the entrance of the garden center, where cameras can be positioned to monitor incoming and outgoing customers, as well as deter potential theft or vandalism. Another crucial area is the checkout counter, where cameras can help prevent employee theft and ensure accurate transactions. Additionally, cameras should be placed strategically throughout the outdoor nursery area to monitor plant inventory and prevent unauthorized access. It is also recommended to have cameras in the parking lot to enhance customer safety and deter car break-ins. Lastly, cameras can be placed in the storage and loading areas to monitor inventory movement and prevent theft. By strategically placing cameras in these areas, garden centers can enhance security, protect their assets, and provide a safe shopping environment for customers.